We all use the internet to complete increasingly sensitive tasks: book doctor’s appointments, file taxes, apply for financial aid. When we do, our data can be tracked from the moment we open our browsers to when we click “book” or “submit.”
This type of data tracking is done by analytics software that organizations install on their websites to gather information about visitors. One common use for these trackers is to help companies “retarget” ads toward people who have already shown an interest in their products or services.
The Markup has been tracking the trackers, and in 2022 we looked deeper into one in particular—the Meta Pixel—that is present on more than 30 percent of popular websites. The pixel collects data on visitors regardless of whether or not they have a Facebook account. Although Meta has policies against collecting sensitive data, our reporting over the past year found that the pixel often did just that, collecting the identities of people who it knew applied for financial aid, gathering the amount of taxpayers’ refunds, and even seeing users’ prescriptions and their answers to questions about addiction and migraine symptoms.
Companies choose to embed the Meta Pixel and can change its settings, and yet, repeatedly, those we found sharing sensitive data through the pixel told us they didn’t know they were collecting it and soon removed the pixel or changed its settings.
As we move into 2023, here’s what organizations (and their employees) can do to investigate whether their company has the Meta Pixel installed and, if so, what information it’s passing to Facebook.
1) Check for the Meta Pixel’s Presence on Your Site
If you don’t know whether your organization has embedded the Meta Pixel on its site, there are simple ways to check.
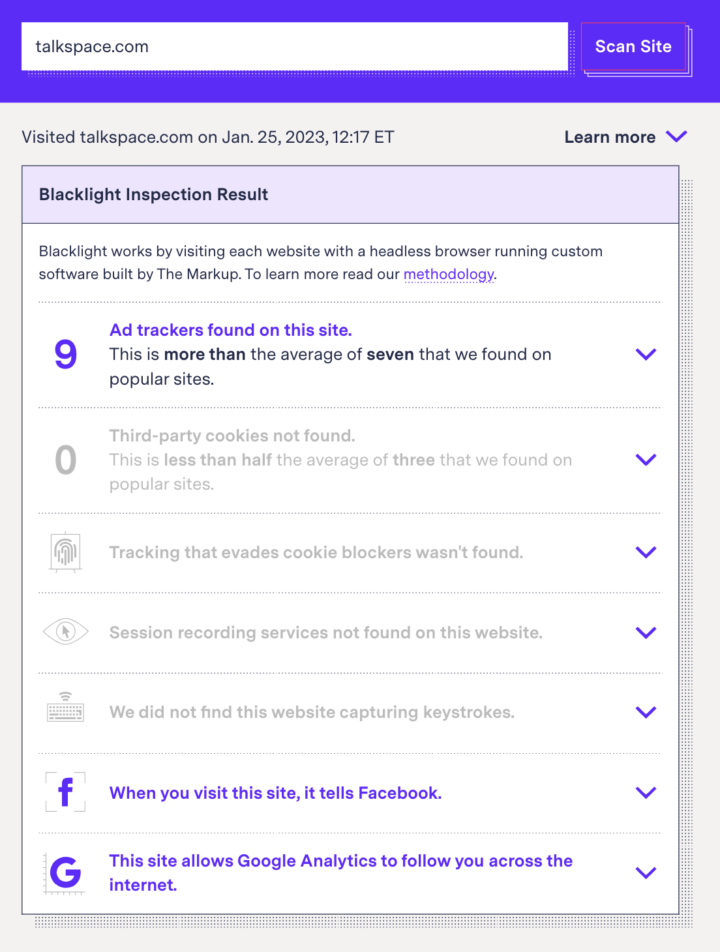
Start with our Blacklight tool. Type in your site’s address, click “scan site,” and Blacklight will let you know which trackers are present, including the Meta Pixel (which Blacklight refers to as the “Facebook pixel”).
If Blacklight’s inspection result says, “When you visit this site, it tells Facebook,” it’s time to get a better idea of what’s actually happening (go to Step 2). If Blacklight doesn’t find anything, it only means that it didn’t find the Meta Pixel on your site, either on the homepage or on a randomly selected internal page linked from the homepage, but we know from testing and reporting that tracking can vary widely across individual pages or URLs of a website. In Step 3, we share how you can check for the pixel on other pages.
You can also ask around at your organization. Coworkers with titles like “web developer” or “paid advertising manager” might be working with the pixel directly, or at least know whether it’s being used.
2) Consider What User Activity on Your Site Could Be Sensitive
Does your organization offer legal services? Provide mental health support? Abortion care? If your organization handles sensitive information, look into the Meta Pixel’s presence—and exactly what data it’s collecting. If you care about user privacy, you’ll want to make sure that sensitive information isn’t being sent to Facebook—and, if people might be revealing sensitive information about themselves solely by visiting your site, you may need to remove the pixel entirely.
We know that in many cases ad tracking is a mandate. If you work for an online clothing store or other e-commerce site, your company might have a whole team dedicated to implementing and optimizing ads through the Meta Pixel. Your company’s website most likely also collects or displays some type of sensitive information, such as people’s credit card details.
Take some time to navigate your organization’s website as if you were a user yourself, considering where you might enter sensitive information, or where it might be displayed to you. This might be clear from the get-go, or it might require some exploring. Either way, take note of which pages ask users for data, particularly through forms or questionnaires. Once you’ve done so, you’ll revisit these pages in steps 3 and 4.
3) Check for the Pixel on Pages with Sensitive User Activity
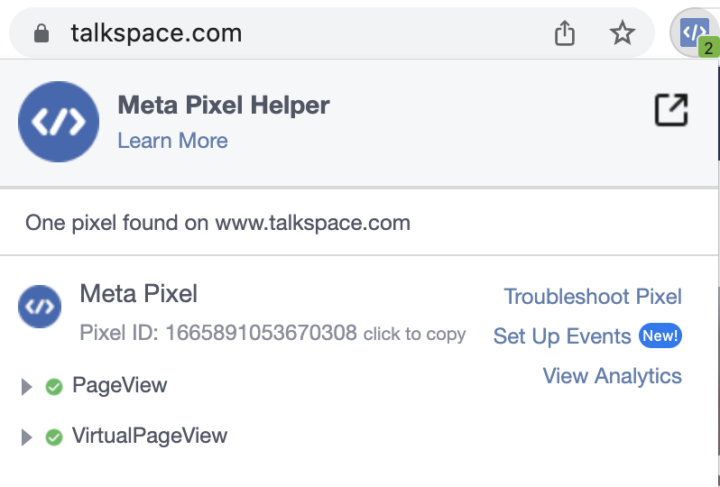
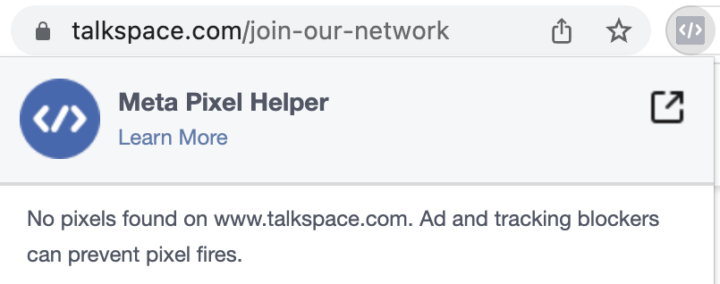
While our Blacklight tool gives a big-picture look at a site’s tracking parameters, Meta itself offers a browser extension that checks whether the pixel is active on a single webpage. Install the extension and head to the pages you identified that could be collecting sensitive information. Then see whether the extension icon lights up blue or remains gray.
If you use an ad blocker or other privacy-oriented tool, you’ll want to turn it off to make sure you’re seeing the full picture of what’s happening on the site.
4) Conduct a Self-Audit of the Data Being Collected
If the pixel is present on the particular page you’re curious about and you’re technically adventurous, you can use your browser’s developer tools to get an idea of whether info displayed on it or entered on its forms is being sent to Facebook.
Markup reporter Todd Feathers walked community and social media manager Maria Puertas, who had never used developer tools to look at web traffic before, through the process. Here’s what she learned:
In this video, we used Chrome’s developer tools to check what data is sent to Facebook by reviewing network traffic. You can follow a similar process on Firefox or other browsers as well, but the information can be a bit harder to read in some cases, and the buttons might be in slightly different spots.
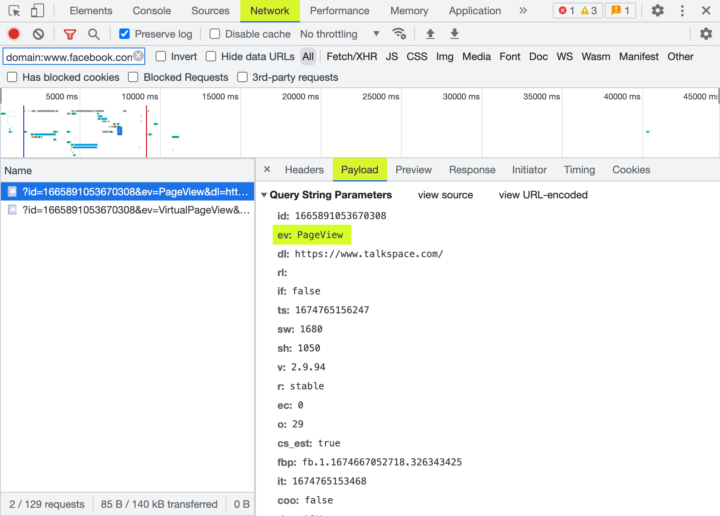
To recap, once you’ve narrowed down the “Network” tab to only show when your website sent information to Facebook (by typing “domain:www.facebook.com” into the search bar), you can click on each row and review the “Payload” tab to see key details about what information was sent. On this tab, look at what’s to the right of ev:.
PageView event highlighted under the “payload” of developer tool’s “network” tab. This event lets Facebook know that a user viewed a particular page.This is the name of an event. The pixel can send data about default, standard, and custom events. The default events are:
PageViewevents: created when the pixel loads after users visit a page; tells Facebook the URL the user is visiting.Microdataevents: generally created shortly after users load a page, and includes information like the page’s title and description.SubscribedButtonClickevents: created after users click on something the pixel detects as a button or link. The information sent to Facebook generally includes the button or link’s text. Sometimes Facebook thinks other elements on the page are buttons or links, even when they’re not. It’s worth clicking on the text of sensitive data on your site to see if it gets sent.
Your site, or some other software that has been added to your site, may be creating events beyond default events, since every website can configure the pixel in its own way. These could be from a set of standard event types or a totally custom event type. We’ve regularly found these nondefault events used to send information to Facebook when users sign up for an account, subscribe to a mailing list, add an item to their shopping cart, make a purchase, or submit a form.
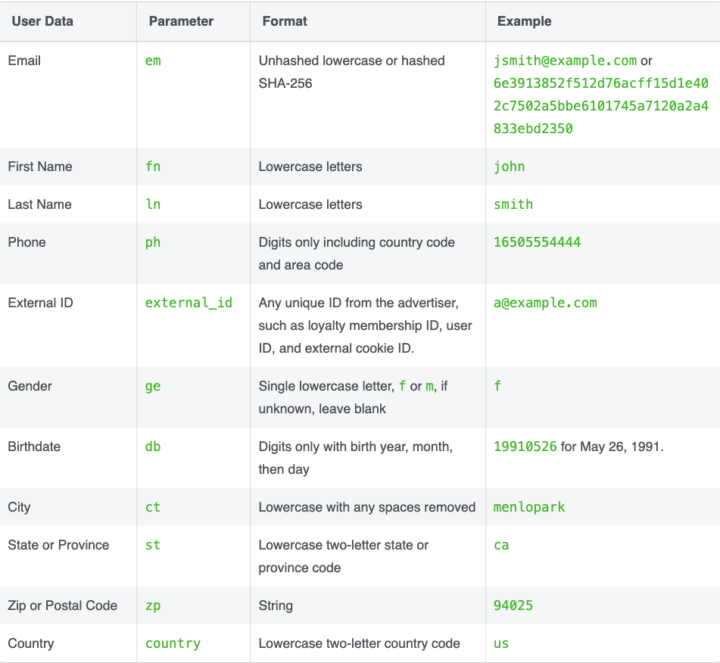
If your website has a form asking users for their name, email address, or phone number, the pixel may send that data to Facebook as well, in any type of event. When you’re scrolling through the “Payload” tab, look for this udff pattern, such as udff[em], udff[fn], or udff[ln].
These are what Facebook calls advanced matching parameters. The letters or numbers in between the brackets are shorthand for the data being sent. For example, em means email. Facebook has a table where you can look these abbreviations up:
You’ll also notice that the whole line says something like:
udff[em]: 6e3913852f512d76acff15d1e402c7502a5bbe6101745a7120a2a4833ebd2350
That long string of letters and numbers is called a “hash,” which is like a more secure pseudonym for the personal information submitted by a user. But even though hashing obscures the data, researchers have shown that hashing doesn’t truly protect people’s personal information. In fact, Meta explicitly says that after getting this hashed information, the advanced matching feature is used to link the information with a specific person.
Note that sometimes a parameter name won’t accurately describe the data sent through that field because a pixel or other code on a site will incorrectly detect the type of information being submitted.
We go further into detail about what we look for when we examine the data being sent to Facebook from a site in our Show Your Work article for our Pixel Hunt series.
5) Take Your Findings to Those Who Can Implement Changes
Now that you have an idea of what information is being collected and where, it’s time to take that knowledge to the people at your organization who can make or approve changes to the pixel’s settings. Whether that’s leadership or a web team, we hope you feel equipped to share your findings.
Don’t be surprised if many people in your organization don’t know about the Meta Pixel. Many of the organizations we found leaking sensitive user information to Facebook seemed to be unaware of what exactly they were doing or the potential ramifications. In certain cases—like that of tax preparation site Ramsey Solutions—companies said they didn’t know they were collecting this kind of data from their users and promptly deactivated pixel tracking parameters.
“We did NOT know and were never notified that personal tax information was being collected by Facebook from the Pixel,” Ramsey Solutions said in an email to The Markup. “As soon as we found out, we immediately informed TaxSlayer to deactivate the Pixel from Ramsey SmartTax.”
Ramsey Solutions wasn’t the only organization that removed the pixel after being contacted by our reporters for comment. After we notified hospitals and health systems of the Meta Pixel’s presence, 35 of 40 removed it either from portions of their websites or altogether. Major tax companies changed the pixels’ settings to capture less data. The U.S. Department of Education changed its pixel’s settings to capture less information on FAFSA applicants.
If You or Your Team Manage Your Company’s Meta Pixel Settings
If you see the pixel collecting more data than you want, there are a few things you can do to protect your users’ data privacy. If you don’t truly need the data, you can remove the Meta Pixel from your site. If you only need the pixel on specific pages, you can configure your site to load the Meta Pixel on only those pages.
If you saw hashed personal information being sent to Facebook through the udff[<value>] parameters, try turning off Automatic Advanced Matching in the pixel’s event’s manager dashboard. If the information is still being sent, it’s likely that another piece of code on your site is responsible.
If data is being sent through SubscribeButtonClick or Microdata events, you can turn that off by tweaking the embed code to turn off autoConfig, as described in Meta’s documentation.
My Organization Doesn’t Employ the Meta Pixel, but I’m Still Concerned About Our Visitors’ Privacy. What Else Can I Do?
The Meta Pixel is just one of many ad trackers that can follow users across the web and potentially collect sensitive information about them. For example, an investigation by The Markup and STAT found 49 out of 50 telehealth websites sharing health data via at least one tracker—from Meta, Google, TikTok, Bing, Snap, Twitter, LinkedIn, or Pinterest—that collected patients’ answers to medical intake questions.
To address other tracking technologies, start by reading through the Electronic Frontier Foundation’s comprehensive guide on better privacy practices for nonprofits.
In 2022, we wanted to find out what the Meta Pixel was actually collecting as people surfed the web. We found numerous instances in which this pervasive piece of code was used in a way that compromised the security of users’ sensitive data. In 2023, we hope that organizations see why it’s time to be proactive about user privacy. If this guide helped you make change within your institution, please let us know: hello@themarkup.org.
Correction
An earlier version of this story indicated that The Markup’s Blacklight tool searches for the Meta Pixel only on a site's homepage. Blacklight searches not only the homepage but also a randomly chosen internal page linked from the homepage.